Human Two
Home >
Huntress CTF > Easy Challenges
Back <> Next
During the MOVEit Transfer exploitation, there were tons of “indicators of compromise” hashes available for the human2.aspx webshell! We collected a lot of them, but they all look very similar… except for very minor differences. Can you find an oddity?
Here we are given a zip file to download. Once unzipped we are given a ton of html text documents and the objective here is to find which one contains the flag.
All of the file sizes are exactly the same, however, using: diff on two of the files reveals that line 36 is different between all of the files.
Example:
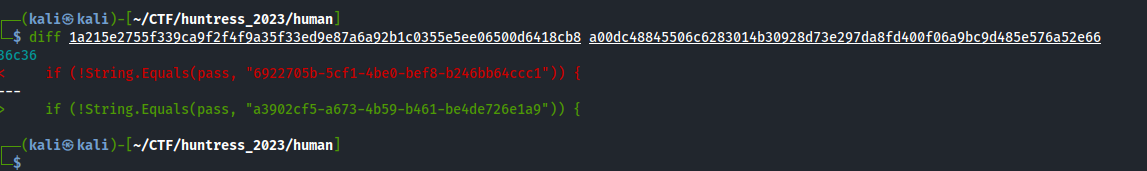
We can then grep for ‘pass’ on that line to identify anything that stands out:
grep pass *
scrolling through we find that one stands out and is much longer than the others:
cc53495bb42e4f6563b68cdbdd5e4c2a9119b498b488f53c0f281d751a368f19: if (!String.Equals(pass, "666c6167-7b36-6365-3666-366131356464"+"64623065-6262-3333-3262-666166326230"+"62383564-317d-0000-0000-000000000000"))
We can then decode the hex values from this to retrieve the flag. Here is another fancy one liner to do it all in one go:
grep pass * | grep -v var | egrep -E '.{200,}' | egrep -oE '\"([0-9a-f+"-]+)\"' | tr -d '"' | xxd -r -p

