Wimble
Home >
Huntress CTF > Easy Challenges
Back <> Next
“Gretchen, stop trying to make fetch happen! It’s not going to happen!” - Regina George, Mean Girls
For this challenge we are given a file ‘wimble.7z’ to download.
Once we extract the archive, we are given the file ‘fetch’. If we inspect the fetch file, we find it is another compressed file which we can extract to receive a bunch of files with the .pf extension.
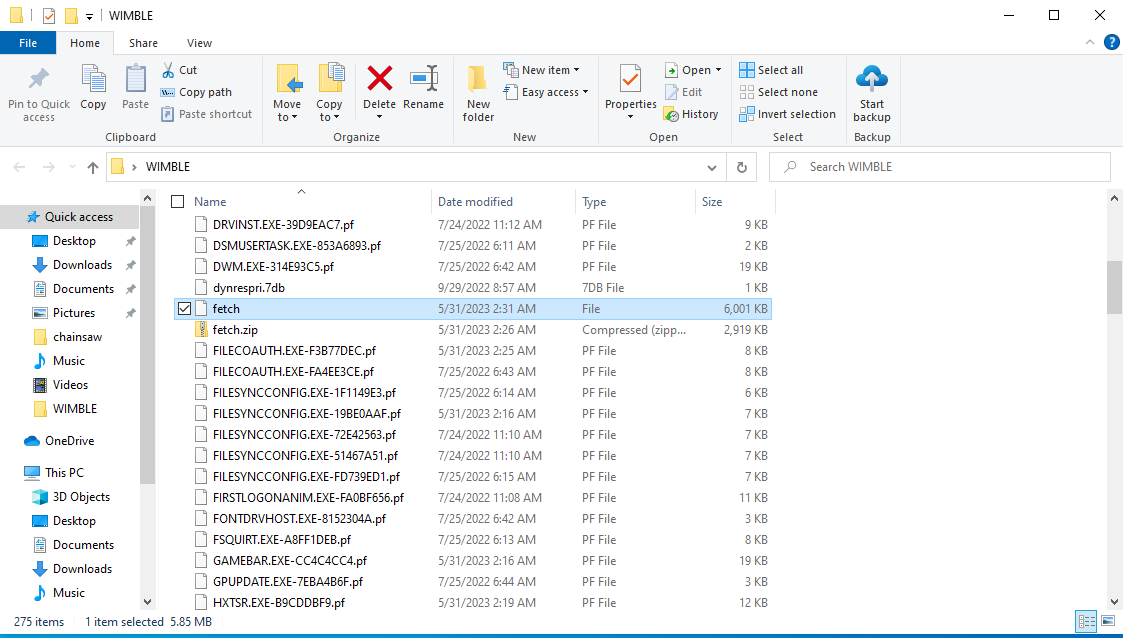
The .pf extension is typically associated with “Windows PreFetch” files. These files are used by the Windows operating system to improve the startup performance of applications. We can use one of EricZimmerman’s tools, prefetch. This tool is designed to work with Windows Prefetch files to provide forensic investigators and analysts with valuable information about a Windows system’s application execution history. The tool can help in various investigative scenarios, including incident response and digital forensics. If we use PECmd.exe in powershell on the folder we extracted from the fetch archive, we can include a findstring and retrieve the flag!
.\PECmd.exe -d . | findstr.exe /i 'flag'