Babel
Home >
Huntress CTF > Medium Challenges
Back <> Next
It’s babel! Just a bunch of gibberish, right?
For this challenge we are given a file ‘babel’ to download. Inspecting the file reveals that it is heavily obfuscated with what looks like base64 encoding, and written in C#. The base64 encoding did not come out to anything usefull at this stage, and we ended up using an online C# complier tool to run the code, and modified the last few lines from:
string YKyumnAOcgLjvK = "lQwSYRxgfBHqNucMsVonkpaTiteDhbXzLPyEWImKAdjZFCOvJGrU";
Assembly smlpjtpFegEH = Assembly.Load(Convert.FromBase64String(zcfZIEShfvKnnsZ(pTIxJTjYJE, YKyumnAOcgLjvK)));
MethodInfo nxLTRAWINyst = smlpjtpFegEH.EntryPoint;
nxLTRAWINyst.Invoke(smlpjtpFegEH.CreateInstance(nxLTRAWINyst.Name), null);
}
}
}
to include a print function to print the decoded lines:
string YKyumnAOcgLjvK = "lQwSYRxgfBHqNucMsVonkpaTiteDhbXzLPyEWImKAdjZFCOvJGrU";
// Decoding the base64 string
string decodedString = zcfZIEShfvKnnsZ(pTIxJTjYJE, YKyumnAOcgLjvK);
// Printing the decoded values
Console.WriteLine("Decoded String: " + decodedString);
// Load the assembly
Assembly smlpjtpFegEH = Assembly.Load(Convert.FromBase64String(decodedString));
MethodInfo nxLTRAWINyst = smlpjtpFegEH.EntryPoint;
nxLTRAWINyst.Invoke(smlpjtpFegEH.CreateInstance(nxLTRAWINyst.Name), null);
}
}
}
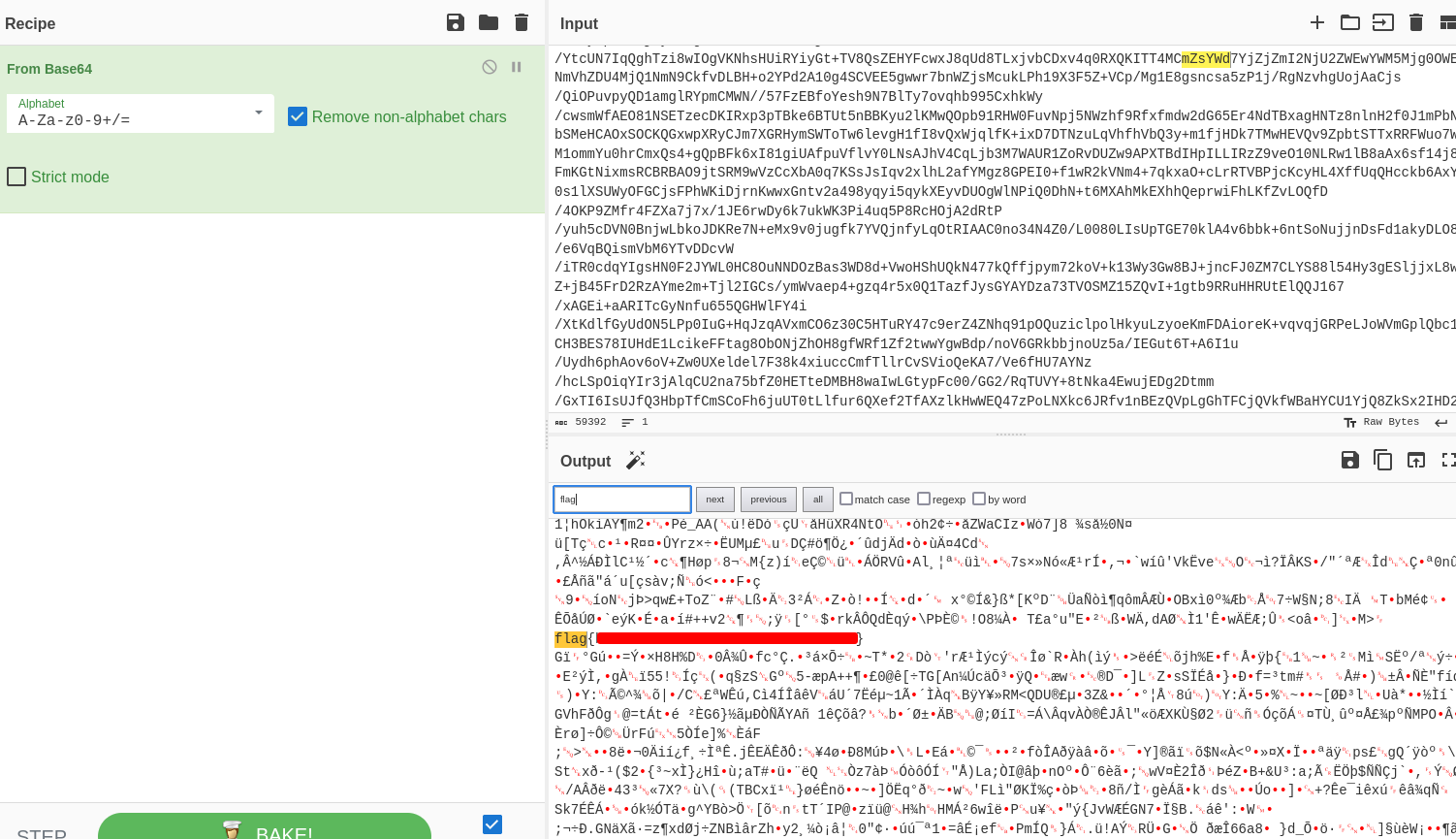
We ran the compiler in the browser, and retrieved the output, which was further obfuscated with base64 encoding.
We then took the base64 encoded output, and decoded it to reveal that this is a compiled binary:
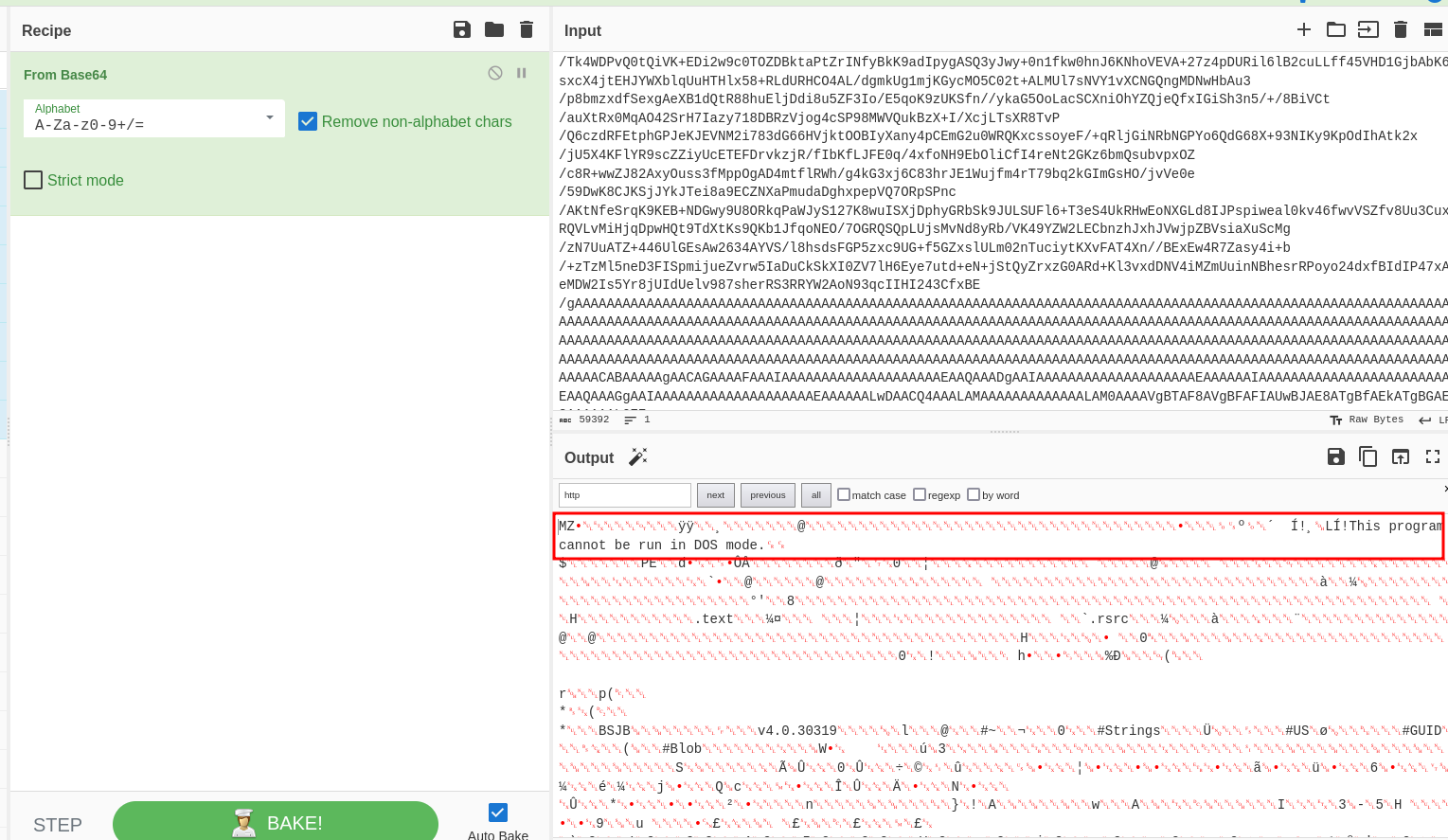
Luckliy, the flag for this challenge can be found in the strings of this output, or by saving it to a file and using:
strings decoded.exe | grep flag