Batchfuscation
Home >
Huntress CTF > Medium Challenges
Back <> Next
I was reading a report on past Trickbot malware, and I found this sample that looks a lot like their code! Can you make any sense of it?
For this challenge we are given a file ‘batchfuscation’ to download and deobfuscate.
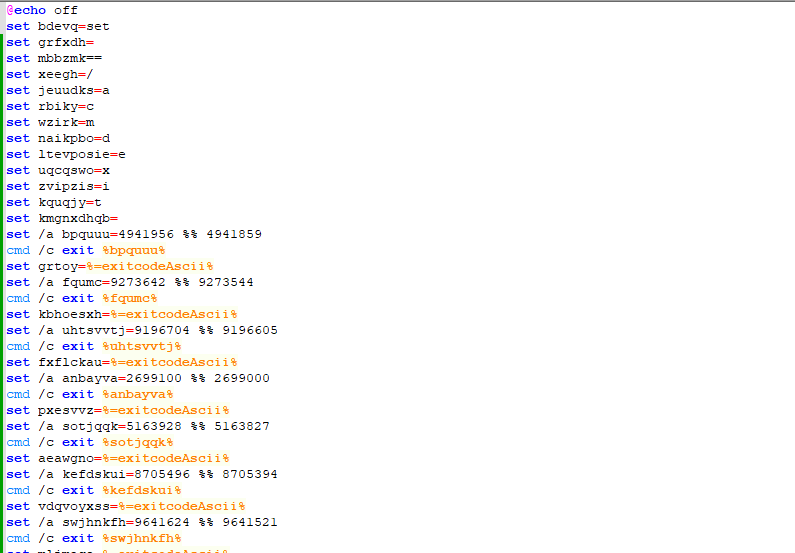
We can see that this is a heavily obfuscated batch script. We began by starting from the top, and using find/replace to begin deobfuscating the initial variables:
set bdevq=set
set grfxdh=
set mbbzmk==
set xeegh=/
set jeuudks=a
set rbiky=c
set wzirk=m
set naikpbo=d
set ltevposie=e
set uqcqswo=x
set zvipzis=i
set kquqjy=t
set kmgnxdhqb=
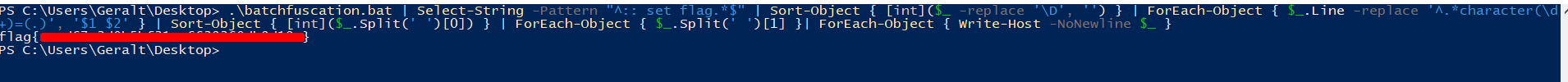
After that the file looked like this:
From here, we took a slightly different approach. We decided to begin decodeing each line by including the following lines in the file, and running it in powershell to view the decoded output line by line:
echo :: whateverline
exit /b 0

Eventually, you will see a set with : ‘flag_characterxx=y’. We can do a find all in current document search, and then copy every instance of flag_character, then paste that in and echo each value when we run the program again:
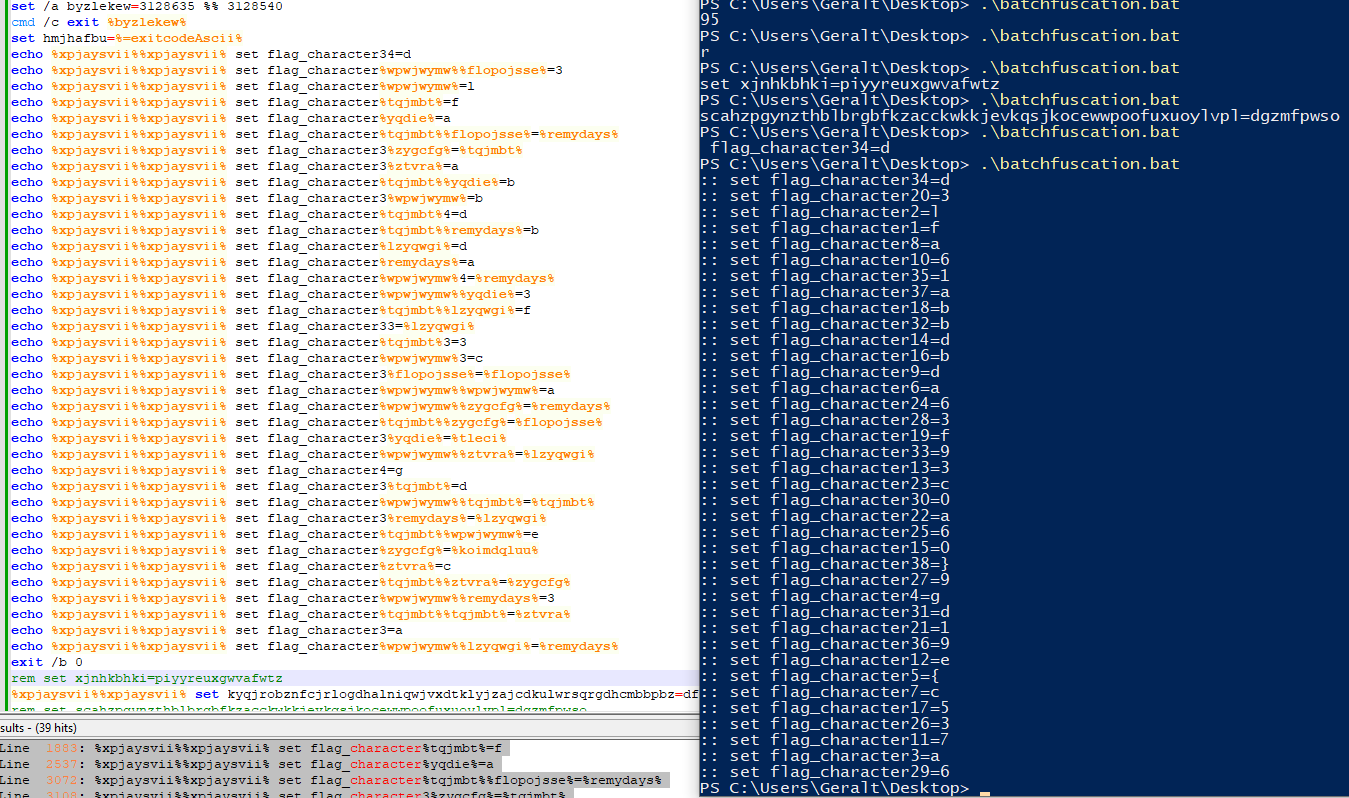
we get the characters for the flag:
20=3
34=d
23=c
30=0
22=a
15=0
38=}
27=9
31=d
21=1
36=9
12=e
7=c
17=5
26=3
11=7
29=6
8=a
10=6
35=1
37=a
18=b
32=b
14=d
16=b
9=d
6=a
24=6
28=3
19=f
33=9
13=3
25=6
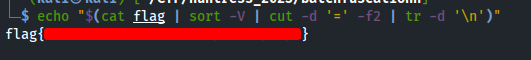
Finally, we placed the values in a flag file, and ran the following command to extract the flag in one line:
echo "$(cat flag | sort -V | cut -d '=' -f2 | tr -d '\n')"
Alternatively, you could add an ’echo ’ to the beginning of every line after line 224 (assuming you’re working with the un-edited file)
Then run the file like so:
.\batchfuscation.bat | Select-String -Pattern "^:: set flag.*$" | Sort-Object { [int]($_ -replace '\D', '') } | ForEach-Object { $_.Line -replace '^.*character(\d+)=(.)', '$1 $2' } | Sort-Object { [int]($_.Split(' ')[0]) } | ForEach-Object { $_.Split(' ')[1] }| ForEach-Object { Write-Host -NoNewline $_ }