MFAtigue
Home >
Huntress CTF > Medium Challenges
Back <> Next
We got our hands on an NTDS file, and we might be able to break into the Azure Admin account! Can you track it down and try to log in? They might have MFA set up though…
For this challenge, we are given a webserver to spin up, as well as NTDS.zip to download.
Once we extract the archive, we receive ntds.dit and SYSTEM. We can use dsinternals to assist with the analysis and the module can be installed by running the following command in a powershell window running as administrator:
Install-Module -Name DSInternals -Force
We can then get the account information from the active directory database (NTDS.dit) using the following command to output the result to a .txt file:
Get-ADDBAccount -All -DBPath .\ntds.dit -Bootkey "$(Get-BootKey -SystemHivePath .\SYSTEM)" > .\output.txt
We know we need to find an Azure admin, so we can search for that within the document, and we get one single result:
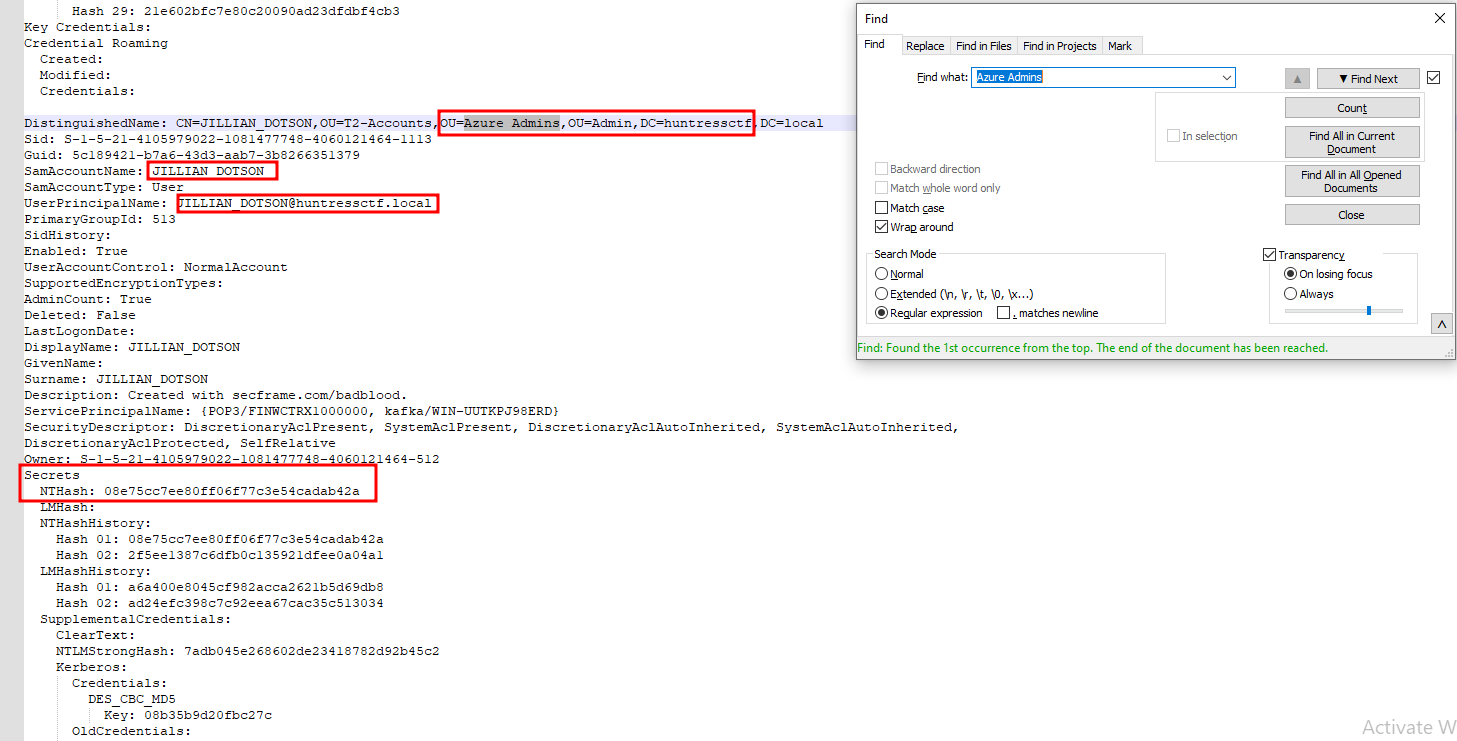
We now know the username, and we can retrieve the password by cracking the NTLM hash. We used crackstation for this.
08e75cc7ee80ff06f77c3e54cadab42a = katlyn99
We can now spin up the webserver and try logging in with the credentials:
huntressctf\Jillian_Dotson
katlyn99
We are then taken to a screen and have to wait for the sign in request to be approved.
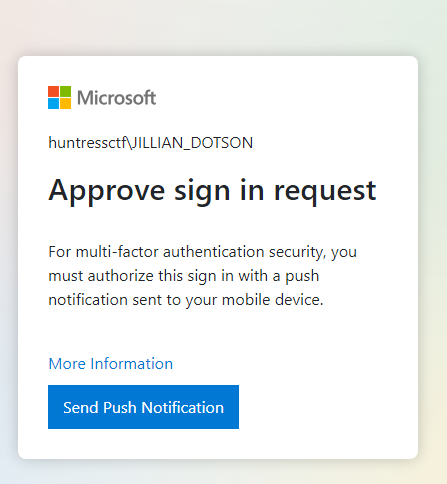
However, if we remember the name of this challenge, we can keep sending push notifications, and eventually retrieve the flag!

