Snake Eater II
Home >
Huntress CTF > Medium Challenges
Back <> Next
Snake Eater II - Revenge of the Snake Eater
The Threat Actor must have gotten word that you had no trouble dissecting Snake Eater. They said this one is a bit more… involved.
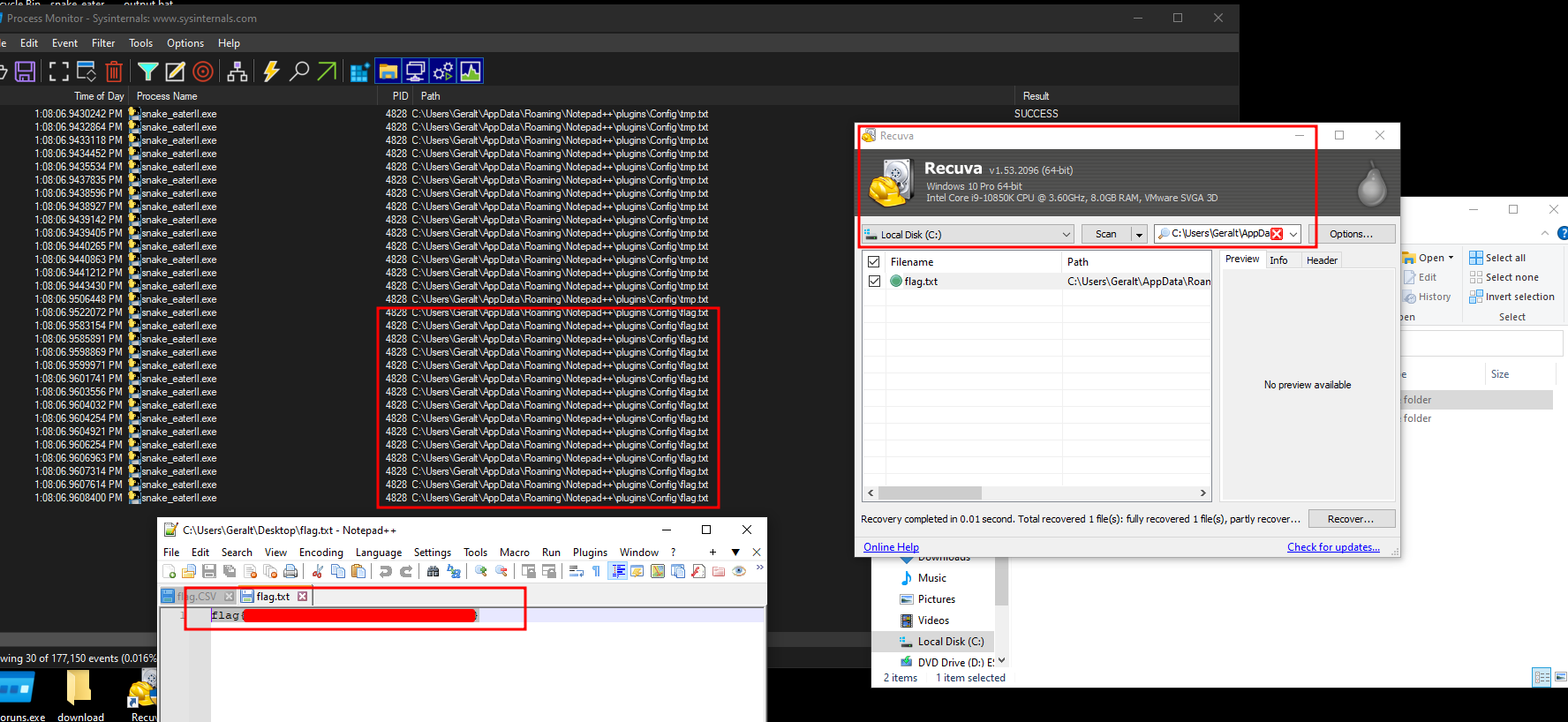
For this challenge, we are given snake_eaterII to download, and inspect. We recalled from the first snake eater challenge, we were able to find the flag using Process monitor, so we decided to start there to see if there was anything interesting to find. We loaded up Process Monitor with the following filters:
Process Name is snake_eaterII.exe
and
Path contains flag
We observe similar behavior to the first snake_eater, however, this time the flag is being written to a file which was created in a random directory (usually somewhere in the C:\Users\user\AppData\Roaming\ path) and then being deleted before the program terminates.
We attempted to use x64dbg to step through the binary and pause the program after it had written the flag, but before it was able to delete it, but we eventually realized that we could simply use a tool to recover the deleted file.
We ran the program while watching process monitor for the exact path for the flag, then used Recuva to recover the deleted file and retrieve the flag!