Black Cat II
Home >
Huntress CTF > Hard Challenges
Back <> Next
Be advised analyst: BlackCat is back! And they’re mad. Very mad. Help our poor user recover the images that they downloaded while browsing their favorite art site. Quickly!
The final challenge!!! For this one we are given the file ‘blackcatII’ to download and unzip.
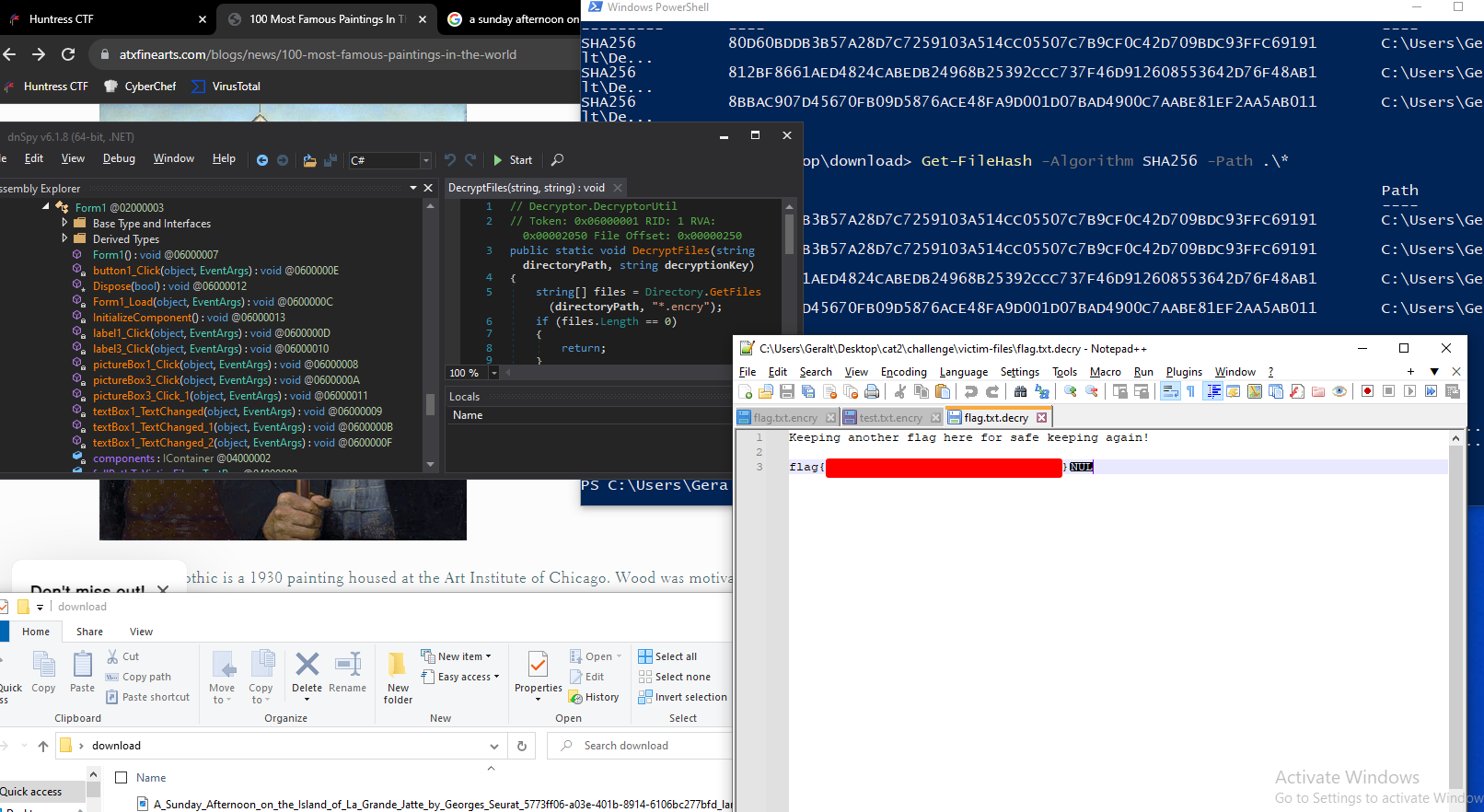
Once extracted, we are given the victim files, and the decryptor.exe, which takes the path to the victim files, and a 64 character password this time:
This binary is written in .Net assembly, so we used DNSpy for analysis.
After inspecting the binary, we found the interesting function called ‘Decrypt Files’:
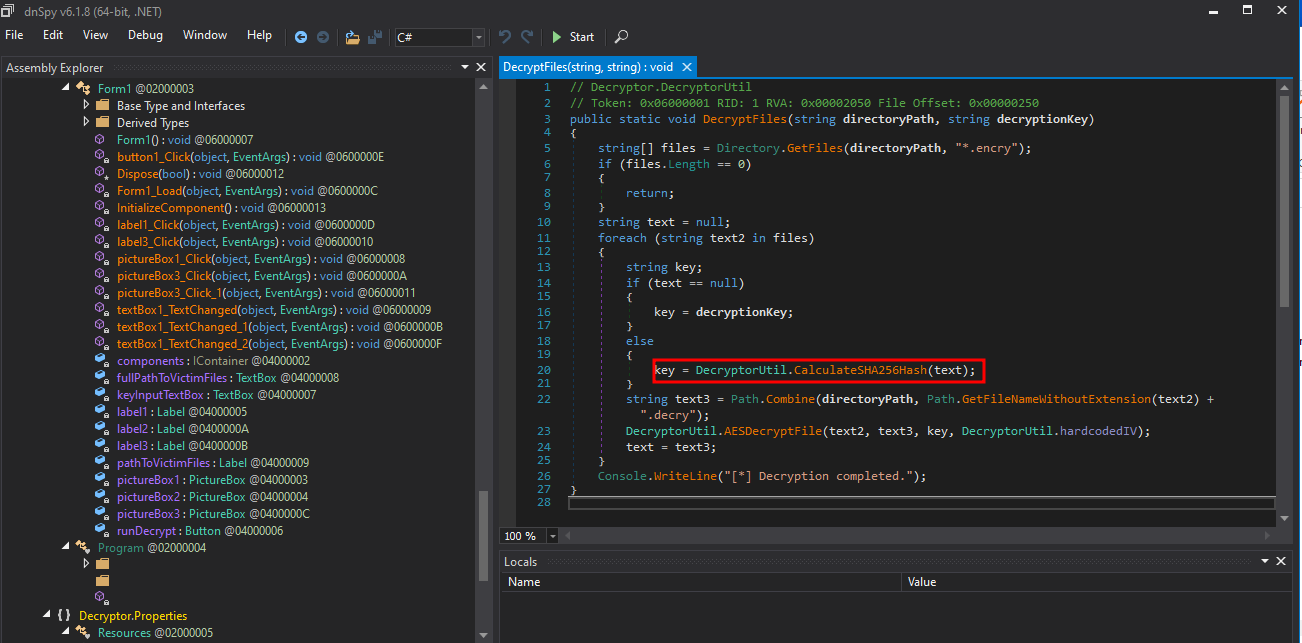
We came to understand that it was using the supplied key to decrypt the first file, and then using the sha256 of the decrypted file as the key to decrypt the next file.
This is important information since we no longer need to figure out the original key, if we can only find the original decrypted image of the first file of the list, which in this case is:
A_Sunday_Afternoon_on_the_Island_of_La_Grande_Jatte_by_Georges_Seurat_5773ff06-a03e-401b-8914-6106bc277bfd_large.jpg
Luckily, this file has a very unique looking name. It still was not easy to find the image however. We began scouring the web for any place that was hosting the image, and checking the hashes to see if they would work…
Eventually, we found this site which contained the photo we needed.
Note: the file name and size matched, but instead of .jpg the extension was .webp. This does not change the hash value.
We then saved the photo, and extracted the hash with
Get-FileHash -Algorithm SHA256 -Path .\*
hash- || 80D60BDDB3B57A28D7C7259103A514CC05507C7B9CF0C42D709BDC93FFC69191 ||
It is also important to note that we needed to remove this encrypted file from the victim folder for this to work properly so the program wouldn’t try to decrypt that file with the hash and throw the whole chain off.
Once we did that, we simply pasted in the hash key and retrieved the flag!