Cipher Pudding
Home >
Cyber Defense CTF > Crypto
Back <> Next
Wings for dessert? But it’s good to the last byte.
❄︎●︎☼︎☼︎☪︎📁︎📂︎🕆︎☼︎✠︎●︎☺︎☼︎☜︎📂︎🗄︎💧︎🕆︎☼︎✞︎💣︎☜︎●︎☜︎✞︎✠︎◻︎☺︎☼︎☜︎📂︎🗄︎💧︎🕆︎☼︎✞︎💣︎🕆︎●︎☜︎✞︎❄︎👌︎☺︎☼︎☜︎📂︎🗄︎💧︎🕆︎☼︎✞︎💣︎☜︎●︎☜︎✞︎✠︎◻︎☺︎☼︎☜︎📂︎🗄︎💧︎🕆︎☼︎✞︎💣︎☜︎●︎☜︎☼︎✠︎♒︎☠︎♋︎🕆︎☞︎⌛︎❄︎🕈︎●︎👌︎💣︎🕆︎🗄︎👎︎✈︎❄︎☞︎☠︎♏︎🕆︎☞︎⌛︎❄︎🕈︎●︎👌︎💣︎🕆︎🗄︎👎︎✈︎❄︎☞︎⚐︎✈︎📁︎☞︎⌛︎❄︎🕈︎●︎👌︎💣︎🕆︎🗄︎👎︎✈︎❄︎☞︎⚐︎✈︎📁︎☞︎⌛︎❄︎🕈︎●︎👌︎💣︎🕆︎🗄︎👎︎✈︎❄︎☞︎☠︎♏︎🕆︎☞︎⌛︎❄︎🕈︎●︎👌︎💣︎🕆︎🗄︎👎︎✈︎❄︎☞︎☠︎🕆︎📁︎☞︎⌛︎❄︎🕈︎●︎👌︎💣︎🕆︎🗄︎❄︎✈︎❄︎☞︎☠︎♋︎🕆︎☞︎⌛︎❄︎🕈︎●︎👌︎💣︎🕆︎🗄︎❄︎✈︎✠︎♒︎☠︎✞︎☜︎✞︎■︎❄︎✠︎◻︎☺︎☪︎📁︎🗄︎🕆︎🕆︎🕈︎♎︎⚐︎✞︎☞︎●︎■︎❄︎✠︎◻︎☺︎☪︎📁︎🗄︎🕆︎☼︎🕈︎♎︎⚐︎✞︎☜︎●︎■︎❄︎✠︎◻︎☺︎☪︎📁︎🗄︎🕆︎🕆︎🕈︎♎︎⚐︎✞︎☝︎☠︎■︎❄︎✠︎◻︎☺︎☪︎📁︎🗄︎🕆︎☼︎🕈︎♎︎⚐︎☼︎☝︎⧫︎■︎❄︎✠︎◻︎☺︎☪︎📁︎🗄︎🕆︎❄︎🕈︎♎︎☠︎✞︎☜︎🕆︎⌧︎💧︎🕆︎☼︎☠︎♏︎🕆︎●︎☜︎✞︎✠︎♒︎☺︎☼︎☞︎🕆︎⌧︎💧︎🕆︎☼︎☠︎♏︎🕆︎●︎☜︎✞︎✠︎♒︎☺︎☼︎☞︎☜︎📁︎💧︎🕆︎☼︎☠︎♏︎🕆︎●︎☜︎✞︎✠︎◻︎☺︎☼︎☜︎✞︎🗐︎❄︎●︎☠︎👌︎♏︎🙵📂︎◻︎✈︎❄︎☞︎☠︎🕆︎📁︎☜︎⌧︎❄︎●︎☠︎👌︎♏︎🙵📂︎◻︎✈︎❄︎☞︎⚐︎✈︎📁︎☜︎⌧︎❄︎❍︎●︎👌︎♏︎🙵📂︎◻︎✈︎❄︎☞︎☠︎🕆︎📁︎☜︎⌧︎❄︎✞︎☠︎👌︎♏︎🙵📂︎◻︎✈︎❄︎☞︎☠︎♏︎🕆︎☞︎🗐︎❄︎✞︎☼︎✞︎☪︎📁︎📂︎⌛︎💧︎🕈︎♎︎⚐︎✞︎☞︎☞︎■︎❄︎●︎☼︎☞︎☪︎📁︎📂︎⌛︎💧︎🕈︎♎︎⚐︎✞︎☞︎☞︎■︎❄︎●︎☼︎☪︎☪︎📁︎📂︎⌛︎💧︎🕈︎♎︎⚐︎✞︎☜︎✞︎■︎❄︎●︎☼︎☞︎☪︎📁︎📂︎⌛︎💧︎🕈︎♎︎⚐︎✞︎☞︎☞︎■︎❄︎●︎☼︎☼︎☪︎📁︎📂︎⌛︎💧︎🕈︎♎︎⚐︎✞︎☞︎✞︎■︎❄︎✞︎☼︎☞︎♏︎♑︎🖬︎🖬︎
On to the last course! Here we are given another encoded message. These symbols are in a font called ‘Wingdings’, as the hint in the prompt suggests. The first step can be decoded using a wingdings decoder such as this one:
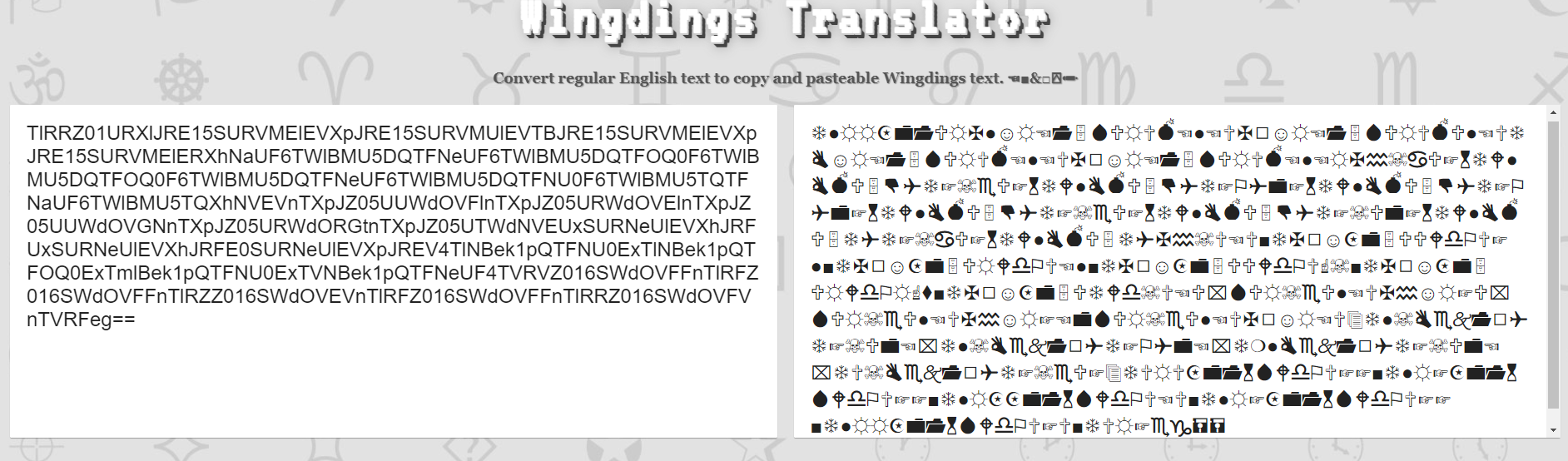
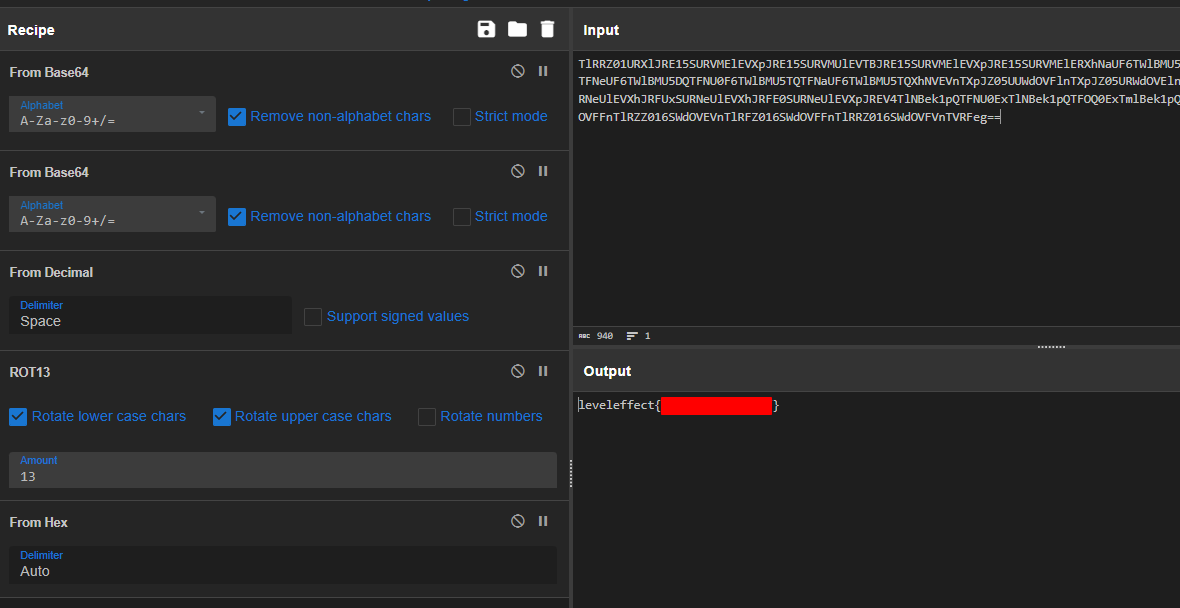
The rest can be decoded in Cyberchef using the following steps:
- from base64
- from base64
- from decimal
- rot13
- from hex