Rock On
Home >
Cyber Defense CTF > Crypto
Back <> Next
Getting it out is the easy part, but good luck getting in.
Here we are given a capture.pcap to download and inspect. Opening the pcap with wireshark we can quickly see some http traffic, as well as a GET request for a flag.zip.
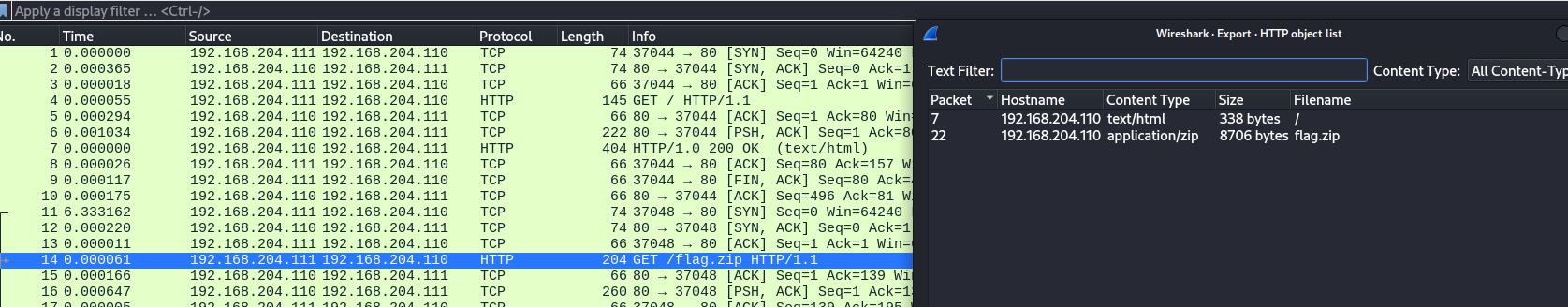
Next, we can export the file to proceed to the next step. Trying to unzip the file reveals that it is password protected. We will need to guess the password in order to continue. We can do this using the Rockyou wordlist and JohnTheRipper.
zip2john flag.zip > zip_hash.txt
john –wordlist=/usr/share/wordlists/rockyou.txt zip_hash.txt
john –show zip_hash.txt
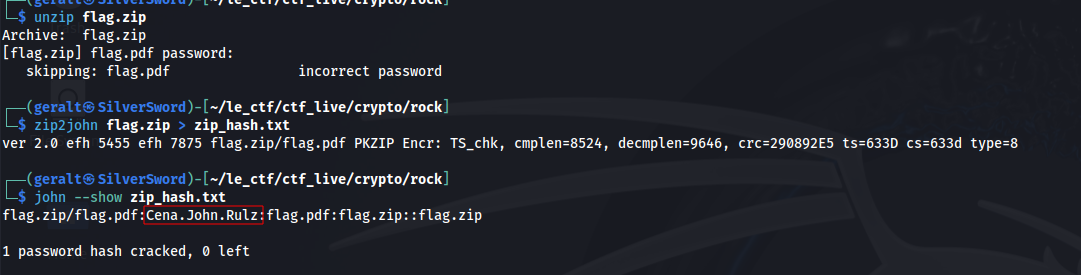
Unzipping this gives us a flag.pdf file which, surprise surprise, is also password protected. We can repeat the process for the pdf:
pdf2john flag.pdf > pdf_hash.txt
john –wordlist=/usr/share/wordlists/rockyou.txt pdf_hash.txt
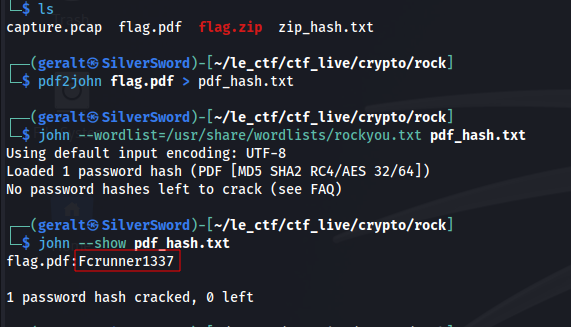
Finally, we can use the cracked password to open the PDF and get the flag:

