Catch the Bandit
Home >
Cyber Defense CTF > Forensics
Back <> Next
Can you catch the bandit and recover the flag?
WARNING - The binary in this challenge is benign but we advise to run it on a VM. Do not run this on your personal machine. Use a VM in the Level Effect CTF course or your own.
For this challenge we are given bandit.exe to download and work with. We don’t really get anything useful by running strings on the binary. We could do some more static analysis, but the intended method is dynamic as the flag is decrypted at runtime.
If we run the binary, nothing seems to happen. However, we can use Procmon and one of several filters:
process name contains/is bandit.exe
path contains flag.txt
These are a few examples.
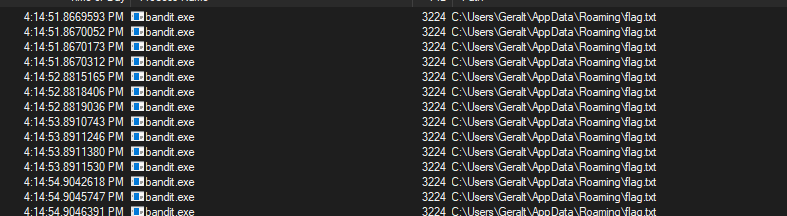
We can quickly see that the flag.txt file is being repeatedly written and deleted to the path C:\Users\%Username%\AppData\Roaming\flag.txt
All we need to do now is recover the file and retrieve the flag! There are many ways to do this but a simple method would be to simply suspend the bandit.exe process in ProcExplorer, and then simply open the file to retrieve the flag!

