Signed and Secured
Home >
Cyber Defense CTF > Networking
Back <> Next
We have intercepted some network traffic after an alert hit from our SOC. Something seems off about some of the traffic here, but we haven’t found anything concrete yet…
Here we are given a file to download; suspicious.pcap.
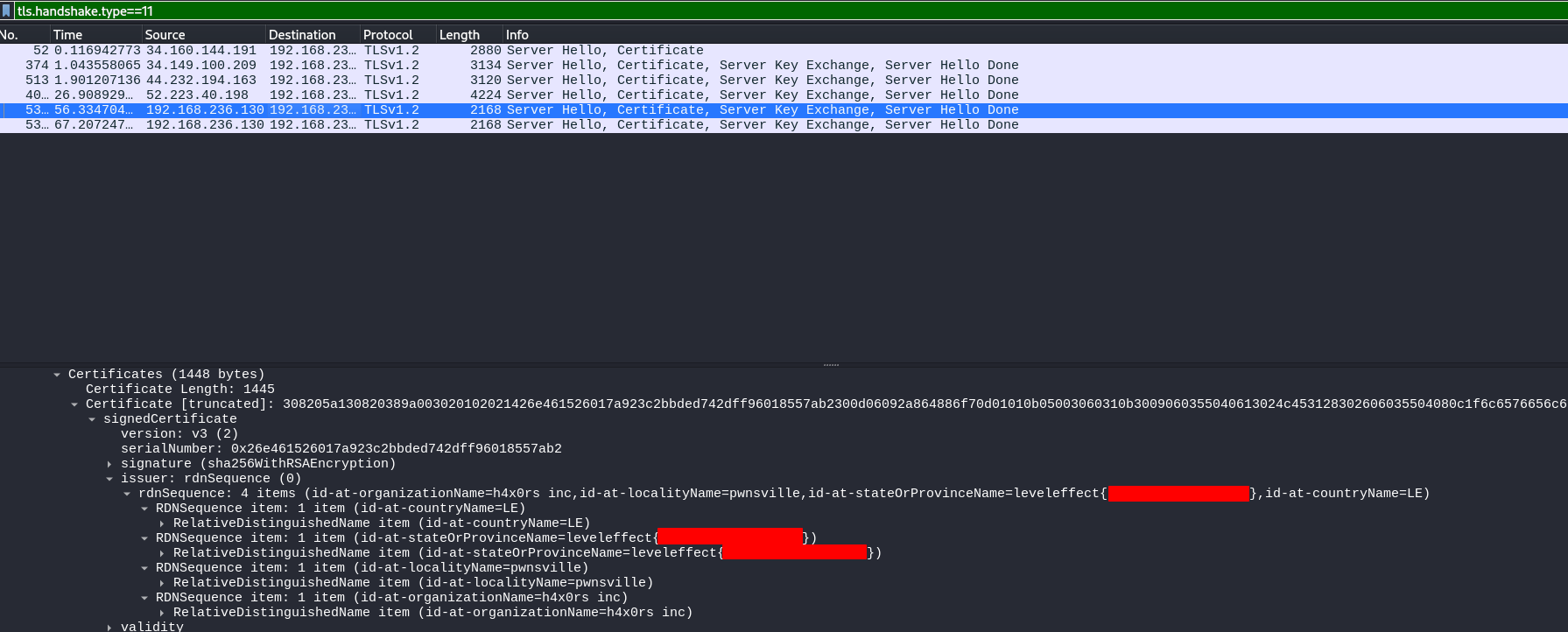
Upon inspection, we can see some http traffic. However, these only lead to dead ends. If we take the name of the challenge as a hint, or just dig around for a while, we will eventually find some tls handshakes. Drilling down into those will show one is an obviously bogus certificate, and the flag can be found in the id-at-stateOrProvinceName field.
Filter:
tls.handshake.type==11