Fragmented
Home >
Cyber Defense CTF > Osint
Back <> Next
It’s a good habit to be suspicious of shortened links, but this one might be worth looking at a little more closely…
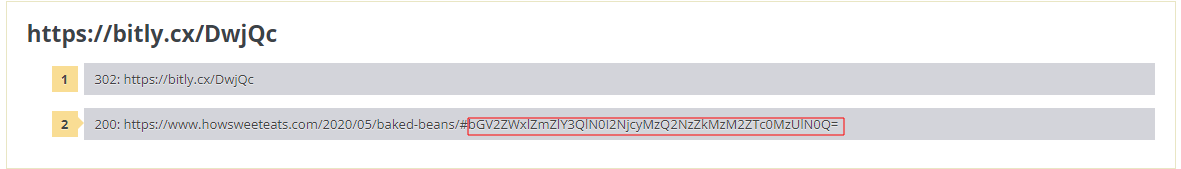
Here we are given a shortened bitly link, which goes to a cooking site. You can either visit the site, or use a url unshortener such as this one. You will notice at the end of the url a ‘#‘followed by a string. This is called a url Fragment Identifier, and it points to a specific section or element within a given webpage. However, if the fragment is invalid, it is simply ignored.
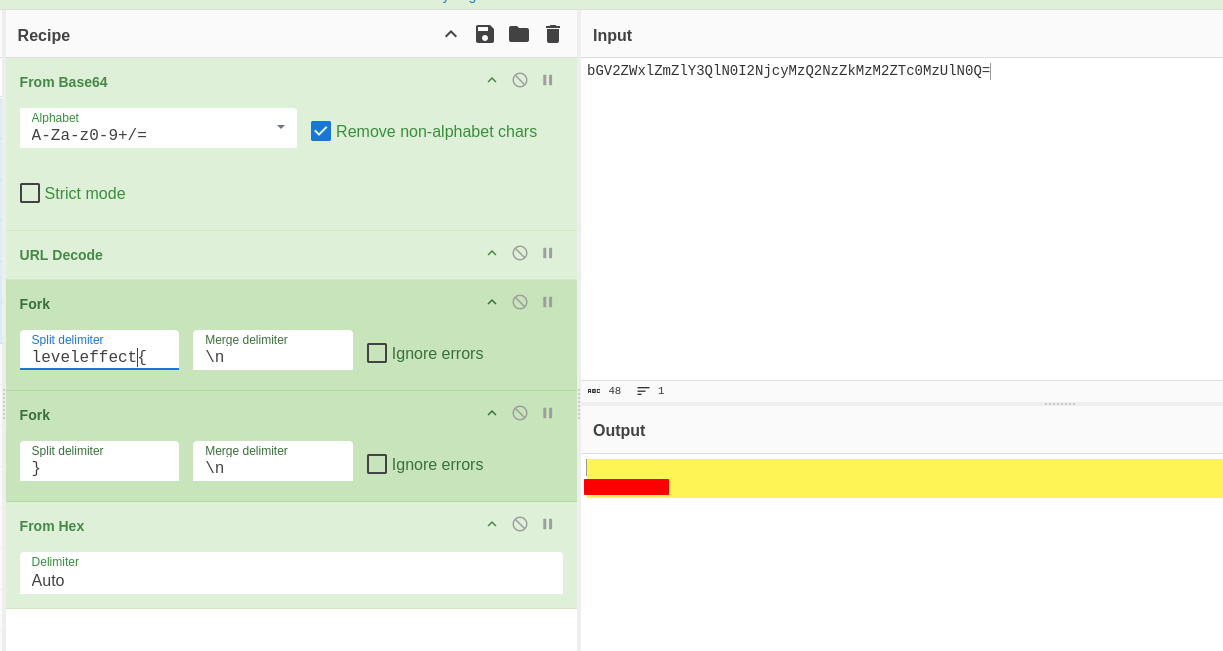
In this case, the fragment contains a string which is base64 encoded:
bGV2ZWxlZmZlY3QlN0I2NjcyMzQ2NzZkMzM2ZTc0MzUlN0Q=
The rest can be most conviniently done using CyberChef
First, we decode the base64, then url decode. The result seems to be a valid flag, however there is still the last part to decode, inside the curly brackets we have some hex that needs to be decoded to get the final part of the flag.