Mangled
Home >
Cyber Defense CTF > Reversing
Back <> Next
Pack? Sure. Unpack? Well…
README - You can access the challenge binary from the Cyber Defense CTF Triage Workstation VM on our hosted platform. You can also download the binary from our GitHub. The password is 00ae587e22a708b1b61d155acfc54152200587af0711c4de16a9e1bfbb922d7f
For this challenge, we are given a packed-flag.exe to investigate.
First, we can check the packing method used using Detect It Easy. This tells us that the packer used was UPX.
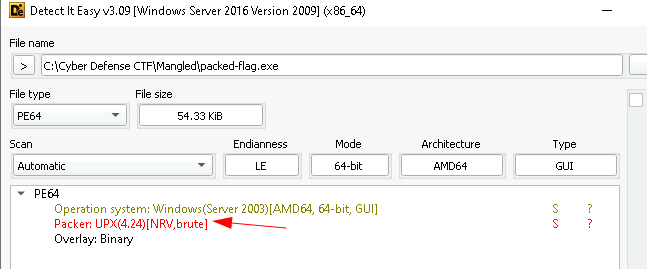
We can try to upx unpack this, but the operation fails and we get an error. Seeing this, we will need to manually unpack the binary in order to retrieve the flag. I found a very helpful and detailed guide to explain this Here.
Essentially, we will be opening the binary using x64dbg, and manually stepping through until we see a jmp instruction with no condition, followed by a long series of null bytes. At that point we will set a break, and step over it once.
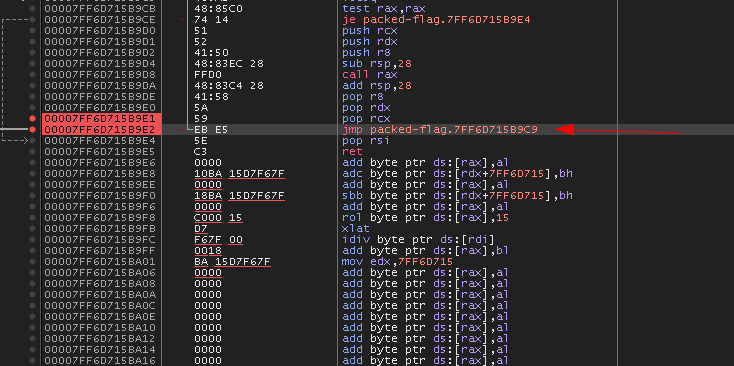
After that, the binary will be unpacked, and we can dump the unpacked binary using Ollydump. However, at this point we will still be missing the imports. We can use Scylla to retrieve the imports by importing our dumped binary, and selecting the ‘Fix Dump’ option. After that you should end up with something like this:
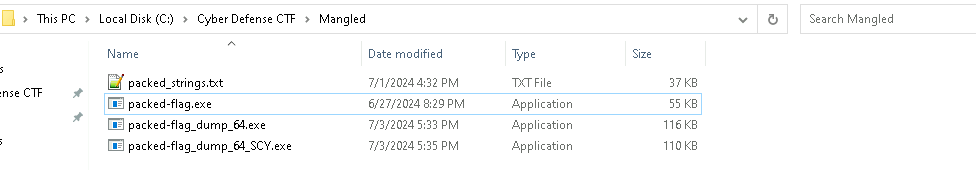
We can open the packed-flag_dump_64_SCY.exe in Ghidra and retrieve the flag: