Shortcut
Home >
Cyber Defense CTF > Reversing
Back <> Next
The key to solving this challenge is LNKing things together!
README - You can access the challenge binary from the Cyber Defense CTF Triage Workstation VM on our hosted platform. You can also download The password is a5e17d51da43123dd1a27bf1001b58c0f721e6a17b31978146bdaf56f620e498
WARNING - This challenge has malware-like behavior involved. DO NOT run this on your personal machine. Use a VM in the Level Effect CTF course or your own.
For this challenge, we are given a flag.ps1 file and a GetFlag shortcut file to inspect.
The flag.ps1 contains some obfuscated powershell. After some deobfuscation we can see that it takes an input parameter, and is comparing the sha256 value against a hardcoded value. If it matches, it uses that as part of the key to aes decrypt the flag. It is also checking to see if there is an environment variable set to the hardcoded value, which base64 decodes to ‘sesame’. If these conditions are met, the decrypted flag gets printed:
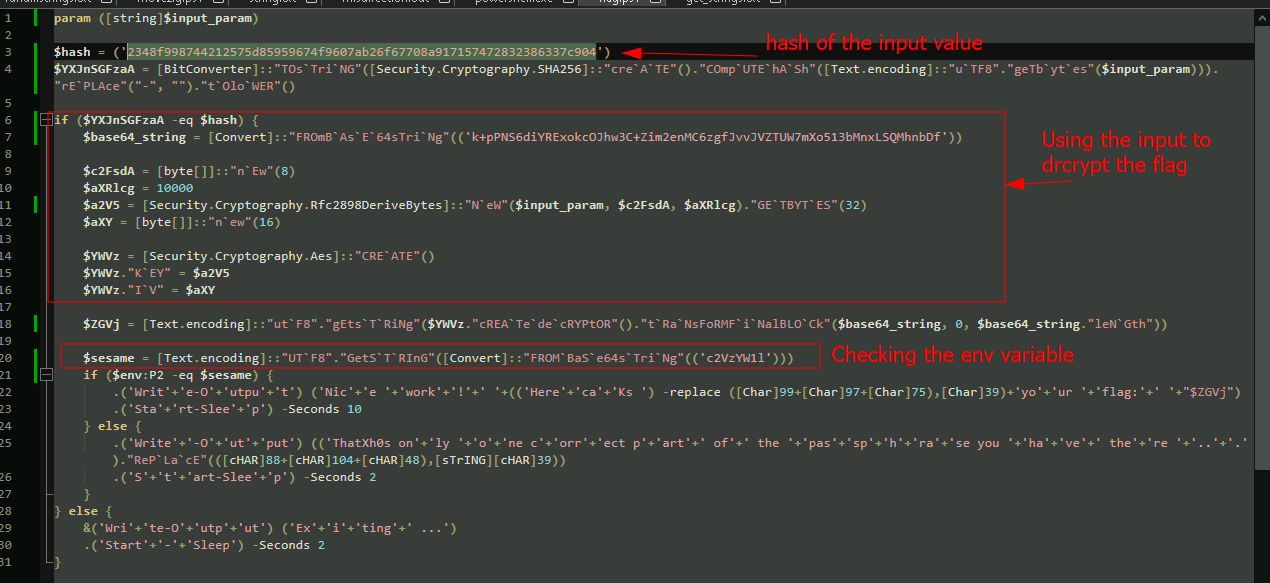
Honestly, I simply base64 decoded the environment variable and was able to guess the input value was supposed to be ‘open’. However, you could also take the hash given and crack it using your method of choice. Crackstation would do the trick as well.
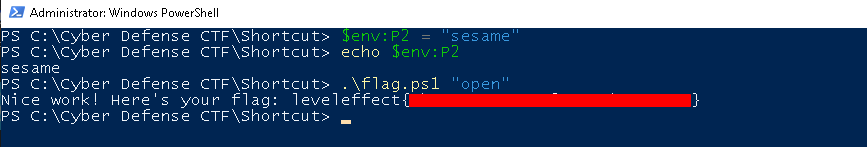
We can set our environment variable to the password in powershell using:
$env:P2 = "sesame"
and then run the flag.ps1 file with the input ‘open’ to retrieve the flag: