The Sprawl 2
Home >
Cyber Defense CTF > The Sprawl
Back <> Next
For these challenges we will be working with theSprawl2.exe
README - You can access the challenge binary from the Cyber Defense CTF - 2nd Phase Triage Workstation VM on our hosted platform. You can also download the binary from our GitHub.
WARNING - This challenge has malware-like behavior involved. DO NOT run this on your personal machine. Use a VM in the Level Effect CTF course or your own.
Sprawl2 Part 1 - The Shapeshifter Enters (Medium)
When you engaged with the virulent Sprawl2.exe program, who were you this time?
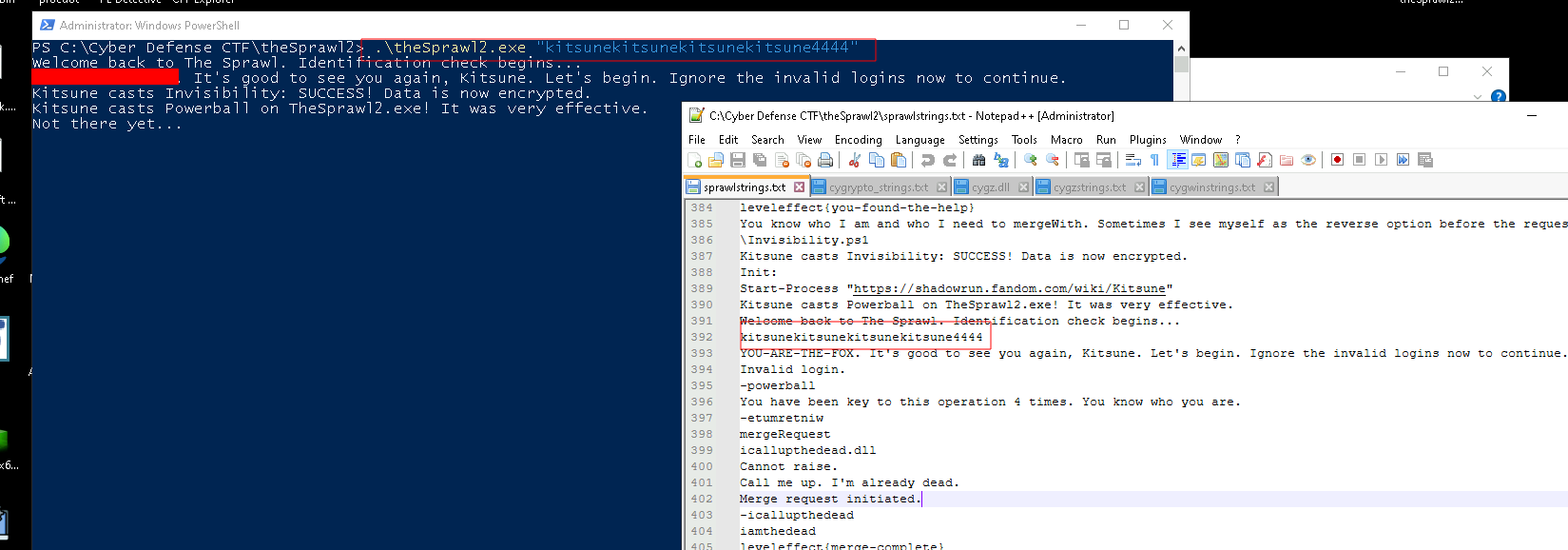
When we run this binary, we get an identity check failed message, at which point kitsune casts Powerball on the binary and the program terminates.
We can dump the strings on the binary, and scrolling through, we see a string: kitsunekitsunekitsunekitsune4444, if we pass this in as an argument when we run the binary, we get the first flag! (It was also visible in the strings dump)
Note: This flag needed to be put inside the leveleffect{} wrapper to be accepted.
Sprawl2 Part 2 - Help is Provided (Medium)
Casting spells together make them much stronger. Combine what you know of from both that were cast and decrypt the helper message.
I dont think I solved the rest of these in the intended way, but I will go through my process regardless.
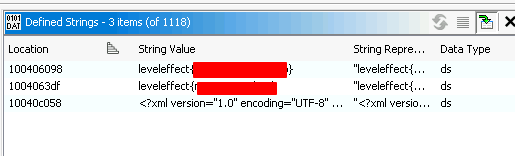
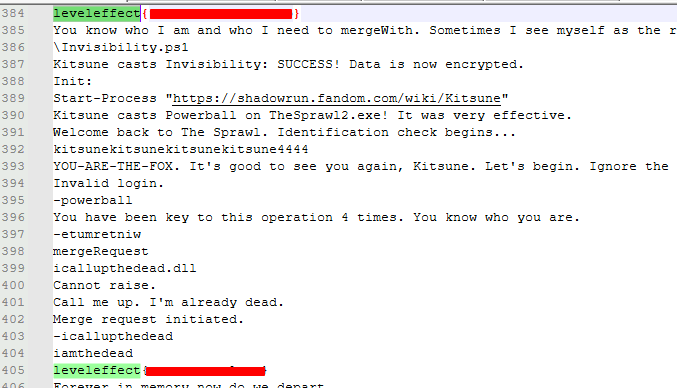
For the second and third challenge, I decompiled the binary in Ghidra, and found the next two flags inside the strings:
Sprawl2 Part 3 - Delete Soul (Hard)
At this point you should be familiar with who you are dealing with. Look up what they want to ultimately achieve. You have a hint on how to configure it by now if you decrypted the previous message.
Same as above for this one, The flag was in the strings I found inside Ghidra:
Also of note, these were present in the strings dump of the binary, I just didnt look for them…
Sprawl2 Part 4 - Memories of it All (Hard)
Were you really the shapeshifter all along? or did you help as someone else without knowing? either way - it’s a memory now.
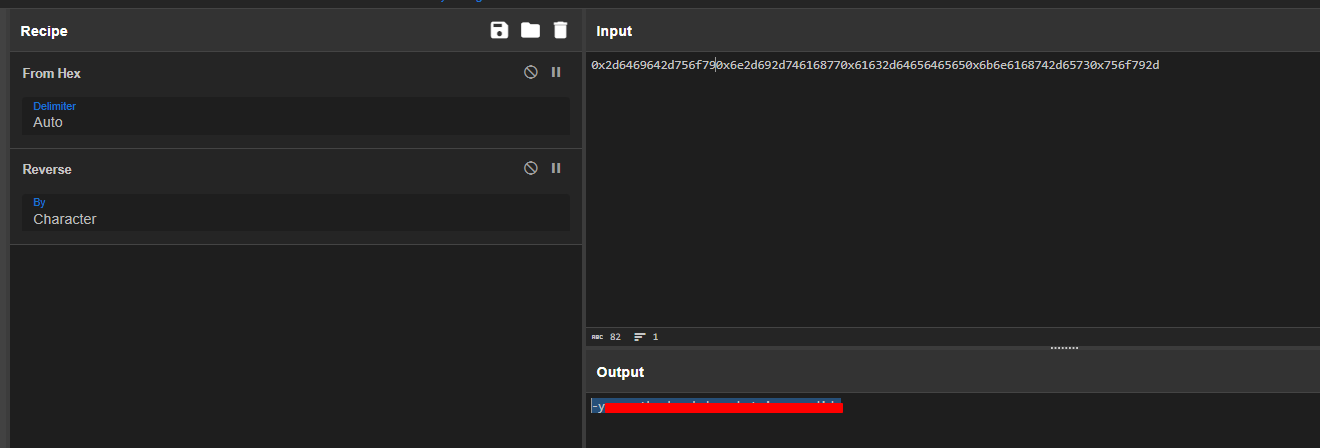
Still looking in Ghidra, we see some hex strings being concatenated:

we can decode these, and reverse them, and piece them back together to retrieve the final flag: